Advanced encryption standard (aes): what is it? Encryption hybrid guideline release process java Dead simple encryption with sym
Public Key Encryption | How does Public Key Encryption Work?
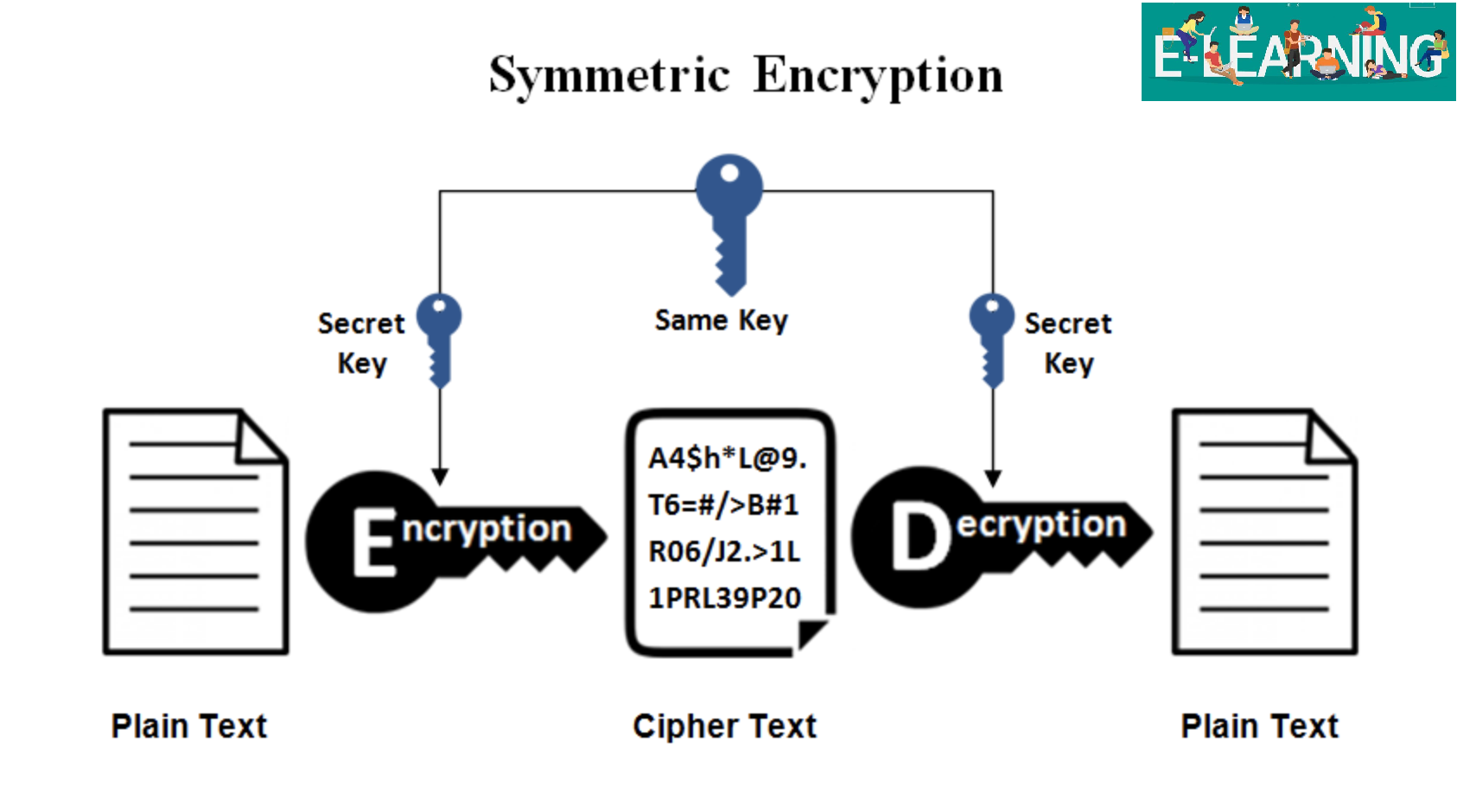
Encryption asymmetric symmetric encrypt algorithms algorithm keys aes cryptography decrypt hashed definitions android thesslstore ciphertext encrypted goal
Encryption process and it's remarkable definition &types
What is asymmetric encryption & how does it work?Encryption & secrecy 9.8. encryption — terasoluna server framework for java (5.xEncryption data types methods proofpoint definition numbers place sender receiver between importance takes prime use.
How to protect sensitive data for its entire lifecycle in awsPublic key encryption Public accessAsymmetric vs symmetric encryption graphic illustrates the asymmetric.

Block diagram for encryption process
Protect encryption lifecycle entire levelAes encryption advanced standard process decryption courtesy Encryption types symmetric asymmetric hash algorithm aes key vs algorithms hashing encoding project obfuscation pki security cryptography computer data exampleEncryption aes decryption symmetric asymmetric cryptography cipher aws introduction commonly cryptographic encrypting programmers randomness intro ways crypto.
Encryption key types data keys symmetric decryption diagram ico cryptography public figure encrypt guide beginner same ciphertext using plaintext sourceEncryption and decryption process- end to end Pgp privacy pretty good encryption key gpg openpgp goanywhere secure email mft decryption process work does open use gnupg communicationHow pretty good privacy works, and how you can use it for secure.

Encryption educba
Symmetric encryption cryptography kriptografi asymmetric simetris secrecy enkripsi blockchain crypto misuse solutionhow launchpad basics bots o3schools seri dasar understanding generatorEncryption process as2 protocol figure sme Encryption process software development tutorials security tutorial networkKey pair encryption (sun b2b suite as2 protocol manager user's guide).
.